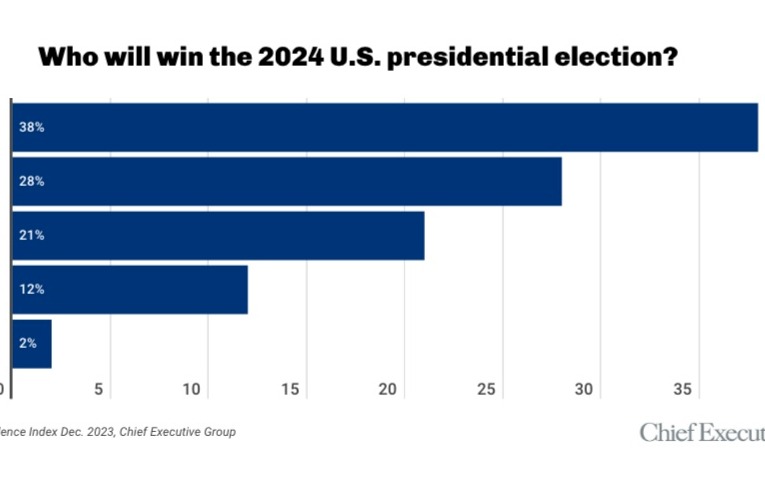
Tim Gallagher spent 22 years in cybersecurity at the Federal Bureau of Investigation, ending up as special agent in charge of the busy Newark, New Jersey office. His job included telling large corporations their computer systems had been hacked by foreign actors—information the FBI often gets from other government agencies.
“I can’t tell you the number of times I have been involved in investigations where I’d go into an enterprise and say, ‘You have a problem,’ and they’d say, ‘No we don’t,’” Gallagher says. “I’d tell them: Keep looking.”
Damage Control
Now head of digital investigations at cybersecurity consultants Nardello & Co., Gallagher tries to keep his clients from getting an unexpected visit from the FBI. That means training C-Suite executives to recognize the multipronged risk cyberattacks pose to their organization and oversee the efforts of the chief information security officer, or CISO, to guard the network and respond to attacks.
The damage hackers can wreak on a corporation isn’t limited to ransomware, as devastating as that can be. (Ask the City of Baltimore, which had to shut down computer systems, including at the City Council and Public Works, during a weeks-long ransomware attack in 2019.) Cybercriminals increasingly are engaging in another form of extortion, where they threaten to leak your internal data to the dark web or a public “shaming site” unless you pay up. Reputational risk is a concern, too: The big corporate law firm Covington this year was ordered by a federal judge to turn over client names to the Securities and Exchange Commission after hackers scraped potentially market-moving information off its servers.
“Everybody’s going to get hit,” Gallagher says. “The idea is if you do get hit, you figure it out as soon as possible. Catch the breach before it becomes a major breach.
”That could mean preemptively shutting down entire computer networks, as Colonial Pipeline had to do in 2021, triggering lines at gas stations around the East Coast. It also probably means engaging crisis communications experts to explain the attack internally to employees and externally to customers, vendors and the public.
What to Ask
The important thing is not to wait until a cyberattack to prepare for it. Nobody expects the chief executive to be an expert on network security but the CEO’s job does include working closely with the CISO to make sure plans are in place and updated frequently.
Questions a CEO must ask include: Is vital data being stored offsite, and how often is that offsite data tested to make sure it isn’t infected with malicious code? What’s the planned response to a cyberattack? Are you testing the plan? What changes are made after a test? “The CEO should be part of those tests and the plans,” Gallagher says.
All this planning can have an impact on the bottom line. Many companies lay off the risk of a major attack by purchasing cyber insurance, but premiums are going up and they’re sensitive to a company’s record and compliance with security standards. Gallagher says Nardello & Co. is seeing some companies dropped by their insurers after several breaches.
Back in the good old days—like a year or two ago—the most common form of attack, “phishing” emails, could be spotted because foreign actors made mistakes in grammar and spelling. Now hackers are using artificial intelligence to construct more authentic-looking emails and machine learning to launch persistent attacks on their targets.
“The good news is the good guys have AI as well,” Gallagher says. In the endless war against cyberintruders, companies are using AI to create programs that detect attacks and deflect them before the real damage occurs.
The post Cyberattacks: Not If, But When appeared first on ChiefExecutive.net.